Alice is a program used to make fictional worlds.
If you wanted to download alice you would go to their website (Alice.org)
The objects alice has to offer would be, animals, people, enviornments, and other kinds of objects.
Alice can be used for fiction world, commericals, tv shoes, and many other things.
All of the objects at the pros of Alice.
The cons would be that it doesnt look real.
When using Alice i used the snowy world, i liked Alice because it was a fun exsperience, probably not, because i dont see myself ever using that kind of program its way to complicated.
Monday, December 14, 2009
Monday, November 23, 2009
Cyberbulling
Article link: http://www.cyberbullyalert.com/blog/2008/10/stories-of-cyber-bullying/
Article Title: The Megan Meier MySpace Incident
Megan Meier was a 13 year old from Missouri who struck up an online friendship on the popular social networking site MySpace with a person she believed was a new boy in her hometown. In actuality, the “friend” was a group of individuals, including adults, who were intent on humiliating the poor girl because of a friendship with another child that had gone awry. Megan was very upset when she found out the truth, then later committed suicide once the friendship had terminated. The horrifying case stunned the community and caused state government officials to pass some of the harshest cyber bullying laws in the country.
I don’t think that it is right for, young kids to start up a relationship with random people they don’t know or haven’t met. I also don’t think it is right for someone who is only 13 years old to have a MySpace account. I understand that she would be upset, but I wouldn’t kill myself over something stupid like that.
The person that they suspect for bullying the young girl was a mother in Missouri who is being charged for first degree murder for bullying the child and leading her to kill herself. The young girl Megan killed herself, because she was stressed and just felt like she couldn’t take life anymore and just wanted to end it all.
Megan could have stood up and told the police or someone that she knew could have helped her out. She also could have just deleted her MySpace or stayed off MySpace for awhile. Also she could have deleted the fake friend. Theirs just so many things she could have done to prevent it from happening.
This could apply to anyone, because anybody could get cyber bullied. You could be getting cyber bullied at school through texts; you could get cyber bullied by people in other states. Its applies to society because everyone can be cyber bullied it just goes on weather or not they keep doing it because the way you react. If you act freaked out, they will continue to do it because they know it scares you. If you act mad and talk crap to them then they will do it to continue to make you mad.
Article Title: The Megan Meier MySpace Incident
Megan Meier was a 13 year old from Missouri who struck up an online friendship on the popular social networking site MySpace with a person she believed was a new boy in her hometown. In actuality, the “friend” was a group of individuals, including adults, who were intent on humiliating the poor girl because of a friendship with another child that had gone awry. Megan was very upset when she found out the truth, then later committed suicide once the friendship had terminated. The horrifying case stunned the community and caused state government officials to pass some of the harshest cyber bullying laws in the country.
I don’t think that it is right for, young kids to start up a relationship with random people they don’t know or haven’t met. I also don’t think it is right for someone who is only 13 years old to have a MySpace account. I understand that she would be upset, but I wouldn’t kill myself over something stupid like that.
The person that they suspect for bullying the young girl was a mother in Missouri who is being charged for first degree murder for bullying the child and leading her to kill herself. The young girl Megan killed herself, because she was stressed and just felt like she couldn’t take life anymore and just wanted to end it all.
Megan could have stood up and told the police or someone that she knew could have helped her out. She also could have just deleted her MySpace or stayed off MySpace for awhile. Also she could have deleted the fake friend. Theirs just so many things she could have done to prevent it from happening.
This could apply to anyone, because anybody could get cyber bullied. You could be getting cyber bullied at school through texts; you could get cyber bullied by people in other states. Its applies to society because everyone can be cyber bullied it just goes on weather or not they keep doing it because the way you react. If you act freaked out, they will continue to do it because they know it scares you. If you act mad and talk crap to them then they will do it to continue to make you mad.
Wednesday, November 18, 2009
Staying Civil Online
It is basically an agreement set to keep you from doing things you aren't supposed to be doing.
1. Behave As Though You Are Communicating in Person
When communicating with someone online, act as if you are talking to that person face to face.
2. Remember That Your Words Are Open to Interpretation
if you post jokes, sarcasm, or other attempts at humor, do not be surprised if someone is offended. Word your postings clearly and carefully.
3. Do Not "Shout" Online
Typing in ALL CAPITAL LETTERS is like shouting and is considered rude.
4. Do Not "Flame" Other Users
In "Net-speak," a flame is a posting that contains insults or other derogatory content. Flamers can be shut out of listservs and chat rooms, and other users can block a flamer's messages.
5. Do Not Send Spam
Spam is the online equivalent of junk mail-uninvited messages, usually of a commercial nature. Most ISPs have strict spam policies. If you are caught distributing uninvited messages to multiple recipients, your ISP may cancel your account. You'll learn more about spam in Unit 14, "Living With Computers"
6. Do Not Distribute Copyrighted Material
Usenet newsgroups and many private Web pages are filled with copyrighted and trademarked text and graphics, posted without the owners permission. Do not think that text or images are "in pubic domain" because you found them on the Internet. Copyrights still apply.
7. Do Not Be a Coward
As a general rule, you should never conceal your identity on the Internet. If you choose to use a screen name do not hide behind it to misbehave
Acceptable Use Policy
An AUP is a set of rules set that you obide by when useing the internet or computer.
To keep kids from doing things they arn't suposed to be doing at school, so they can concentrate on their school work. No bypassing any filters, because it slows down the server. Don't download music, games or other things onto your laptop, because it casues it to run slower. Don't go to any perverted sites, it might cause a virus to be put onto your laptop. Don't be on anything your not suposed to be on, because link is always watching. Also if you break your laptop dont try and fix it yourself take it to link to fix it.
Have a program set up on the computer to watch and record everything to see how the workers are spending there time and make sure they get there work done.
To keep people from doing stuff there not suposed to be doing, so that they can get what needs to be done first instead of wasting there boss or techers time doing other stuff.
I wouldnt have any rules or requlations because i think its kind of an invasion of privacy, as long as there work was getting done i wouldnt care.
Emoticons
An emotion is something that describes how you feel.
An emoticon is something is a expression to show how you feel.
10 examples of emoticons and what they mean are:
=) happy
=( sad
='( crying
= ? confused
;) winking
=-OWW surprised
=-) happy with nose
=-( sad with nose
=D super happy
=V=- a man with an aligotor on his head
An acronym is a shorter version of a phrase
10 appropriate examples texting/IMing acronyms are:
LOL - laugh out loud
BRB - be right back
BBL - be back later
G2G - got to go
L8R - later
2day - today
B4 - before
R - are
Y - why
ILY - i love you
An emoticon is something is a expression to show how you feel.
10 examples of emoticons and what they mean are:
=) happy
=( sad
='( crying
= ? confused
;) winking
=-OWW surprised
=-) happy with nose
=-( sad with nose
=D super happy
=V=- a man with an aligotor on his head
An acronym is a shorter version of a phrase
10 appropriate examples texting/IMing acronyms are:
LOL - laugh out loud
BRB - be right back
BBL - be back later
G2G - got to go
L8R - later
2day - today
B4 - before
R - are
Y - why
ILY - i love you
Monday, November 9, 2009
1. What is HTML? It is the predominate markup lanage for web pages.
2. What is a tag? It is used to start and finish a phase in HTML.
3. Explain "open" and "close" tags An open tag is at the begining and is used to start the phase and a close tag is at the end and is used to end the phase
4. Steps to create a HTML site (BE VERY THOROUGH!!! I should be able to create my own site from your instructions on this one!) Start a notepad document, then look up HTML codes in google, next use codes on the HTML code site you found to create your site.
5. Give 3 websites that give good examples of HTML tags to copy and paste http://www.quackit.com/html/codes/
http://www.web-source.net/html_codes_chart.htm
http://www.w3schools.com/html/html_colors.asp
6. How do YOU feel about HTML? What did you know already? What do you know now? Will this help you with anything in the futre? Why/Why not? It is pretty easy if you know what your doing, i know the baisc things because my mom does HTML all the time for work, i know basicly the same thing i already knew, not really because i already knew what to do in the first place.
2. What is a tag? It is used to start and finish a phase in HTML.
3. Explain "open" and "close" tags An open tag is at the begining and is used to start the phase and a close tag is at the end and is used to end the phase
4. Steps to create a HTML site (BE VERY THOROUGH!!! I should be able to create my own site from your instructions on this one!) Start a notepad document, then look up HTML codes in google, next use codes on the HTML code site you found to create your site.
5. Give 3 websites that give good examples of HTML tags to copy and paste http://www.quackit.com/html/codes/
http://www.web-source.net/html_codes_chart.htm
http://www.w3schools.com/html/html_colors.asp
6. How do YOU feel about HTML? What did you know already? What do you know now? Will this help you with anything in the futre? Why/Why not? It is pretty easy if you know what your doing, i know the baisc things because my mom does HTML all the time for work, i know basicly the same thing i already knew, not really because i already knew what to do in the first place.
Wednesday, October 21, 2009
Ethernet Cables
The purpose of an ethernet cable is to conect computers to a server or to conect a computing device to something.
You will need cable, wire cutters, and 2 RJ45 jacks.
To wire the Ethernet cable to the computer network, first cut off 2 inches (5.1 cm) of the cable sheath using the wire cutters. Next, untwist the pairs of wires and align them by color. Trim all wires to equal lengths, leaving about a half-inch (1.3 cm) of the wire exposed, and insert the wires into the RJ45 plug, making sure they are in the correct order. Use the RJ45 crimper to crimp the plug, and be sure the wires come to the front of the plug, touching the metal contact in the plug. Now cut the cable, and repeat the procedure for the second RJ45 plug. (COLORS: Light Orange, Dark Orange, Light Green, Dark Blue, Light Blue, Dark Green, Light Brown, Dark Brown.)
You use a wire tester and plug the ethernet cord up to both ends and if it flash's green it works if it flash's green and red it doesnt work.
It wasn't to hard i messed up once, but i got it the second time.
Just keep trying until you get it, its not hard if you know what your doing.
Monday, October 19, 2009
Post #3
1. They allow many users to access programs and data st the same time.
2. They allow users to share peripheral devices, such as printers and scanners.
3. they make personal communications easier.
4. they make it easy for users and administrators to back up importtant data files.
WANs - two or more LANs connected together
LANs - network of computers that are relatively near each other and are connected.
Star

Bus

Ring
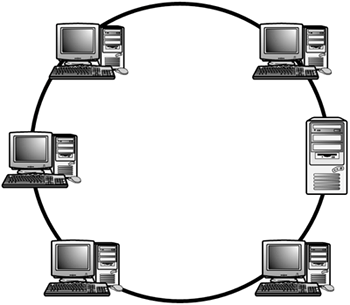
1. File Server
2. Network Server
3. Application Server
4. Server
Client Server Networks - computing or networking is a distributed application architecture that partitions tasks or work loads between service providers and service requesters, called clients
Peer To Peer Networks- commonly abbreviated to P2P, distributed network architecture is composed of participants that make a portion of their resources directly available to other network participants, without the need for central coordination instances
2. They allow users to share peripheral devices, such as printers and scanners.
3. they make personal communications easier.
4. they make it easy for users and administrators to back up importtant data files.
WANs - two or more LANs connected together
LANs - network of computers that are relatively near each other and are connected.
Star

Bus

Ring

1. File Server
2. Network Server
3. Application Server
4. Server
Client Server Networks - computing or networking is a distributed application architecture that partitions tasks or work loads between service providers and service requesters, called clients
Peer To Peer Networks- commonly abbreviated to P2P, distributed network architecture is composed of participants that make a portion of their resources directly available to other network participants, without the need for central coordination instances
Tuesday, October 13, 2009
GRANITE BAY WOMAN ADMITS TO DISTRIBUTING “KNOCK OFF” GOODS
Bunifull adimitted to selling counterfeited handbags and wallets, trademarked by, Gucci, Coach, Prada, Burberry, Kate Spade, Chanel, and many others. The defendant sold the products for cash, she admitted from the time of June 2006 through August 2007 she made a total profit of $184,046. She is faces a maximum of 10 years in prison and up to a fine of two-million dollars. She will find out what she is sentenced to November 30, 2009.
Friday, October 9, 2009
Post #1
What is the purpose of a blog? What pros and cons do you see about blogs? Are they safe? Why/Why not. Explain how blogs could be used as an educational tool.
The purpose for a blog is for you and everyone else to share information with someone. Pros for blogs i think would be that they are helpful and teach you information you may or may not know, and i dont think that theres any cons about blogs. Blogs are say as long as you dont post personal information about yourself or anyone else. The reason i think there safe is because you cant really get anything useful out of blogs unless someone is telling you about themself or another person. Blogs can be used educationaly because you can post information for schools on them or talk about a project or assingment in a class. Also they can be used to update you on certain events that are coming up.
The purpose for a blog is for you and everyone else to share information with someone. Pros for blogs i think would be that they are helpful and teach you information you may or may not know, and i dont think that theres any cons about blogs. Blogs are say as long as you dont post personal information about yourself or anyone else. The reason i think there safe is because you cant really get anything useful out of blogs unless someone is telling you about themself or another person. Blogs can be used educationaly because you can post information for schools on them or talk about a project or assingment in a class. Also they can be used to update you on certain events that are coming up.
Subscribe to:
Comments (Atom)



